Security is a critical aspect of any distributed application model. Most of the firms have a centralized repository of the users in LDAP servers like Active Directory, TDS, Open DJ etc.
Activity :
To Integrate Tivoli Directory Server LDAP with Websphere Application Server as Federated Repository
Assumptions :
a) Tivoli Directory server is allready Installed and users are avaliable in it ( Note Any LDAP ie Active Directory , TDS , OpenDj , Sun Directory Server etc can be used )
b) Websphere Application Server is installed and profiles and servers created and running .
c) The TDS Ldap server should be reachable from the DMGR and the Nodes .. so you can test it using telnet command
From Dmgr and Node check telnet to LDAP at Port 389 ( or which ever port its is running)
Eg : telnet <Ldap IP> 389
d) In this example I have a Dmgr , Nodeagent and a server and will be integrating the Dmgr with TDS LDap
Steps to Integrate LDAP with WAS
Step 1: Details from the LDAP Team.
Before beginning the Ldap Integrating there are a few information which are needed from the LDAP team ( If its not managed by you )
Basic Details needed :
Hostname/IP address of TDS Server : 10.0.0.15
Port No : 386 ( non SSL)
Bind DN : cn =root
Bind Password : password
Base Dn: dc=ibm,dc=com
Additional properties may be needed depending on your env like
User Filter:
Group filter:
User ID map:
Group ID map: etc..
But in my case its not needed as most are default
NOTE : Ensure that the WAS admin user which we logged in the WAS console with ie wasadmin is unique in both the Filebased and in LDAP ie the user wasadmin should not be avaliable in the LDAP as its allready there in the FileBased Registry
And If “wasadmin” is also there in LDAP , then there will be conflict and we will be prevented to login to the admin console as “wasadmin” post the Integration with TDS.
As a best practice , keep wasadmin intact but create another user in the LDAP and later add this use to the admin group from the was console .
For eg I have created “webadmin” as an user in the LDAP which I will add to the was administration group after the WAS integration wth LDAP in this article
This is applicable for all the users in the WAS and LDAP. It should be unique in the repositories
Step 2: Validating using LDAP Browsers
a) Downlaod the Ldap Browser and extract it . Then Launch the “lbe.jar”
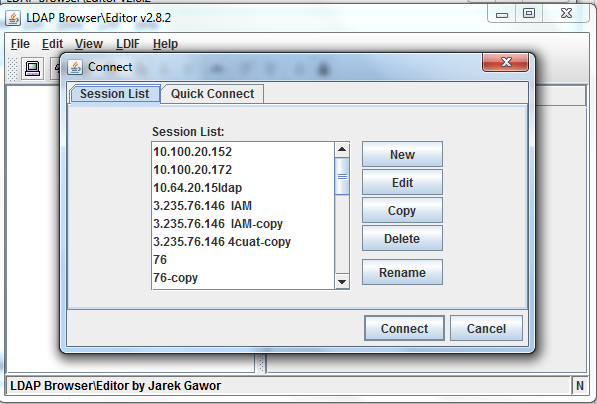
b) Go File >> New
c) Give a name to the connections for recognition . I have entered TDSLDAP
d) Go to “Connections” tab
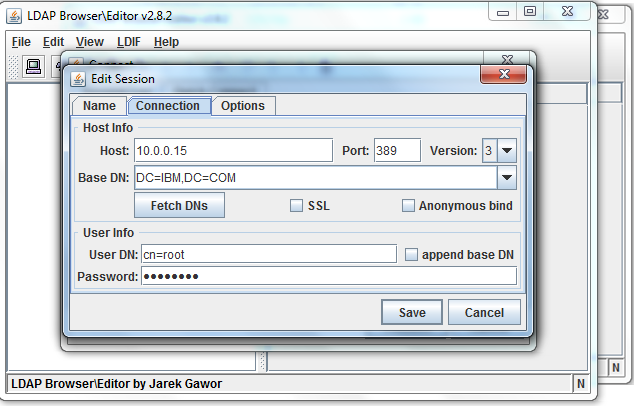
1) Enter the IP Address(10.0.0.15) Port No (389) and click Fetch DN .
2) Select dc=ibm,dc=com
3) Uncheck “Anonymous bind”
4) Enter username “cn=root” and password = password
5) Click Save and then Connect
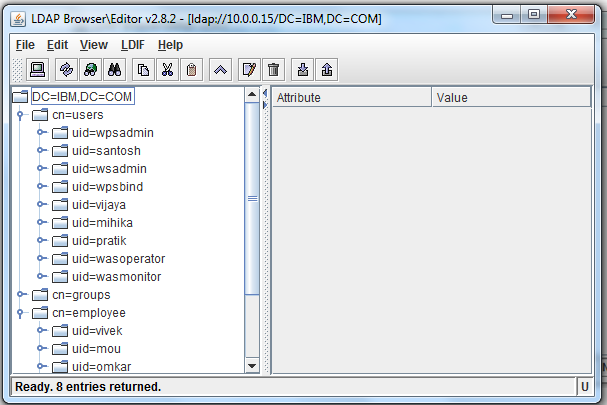
e) We will see all the users which are there in the Ldap in the Ldap Browser console
Step 3: Once all the information is available and validated, we can proceed with the integration of Ldap with WAS
Step 4: Login to the WAS Admin console with wasadmin user
url :https://10.0.0.15:9043/ibm/console
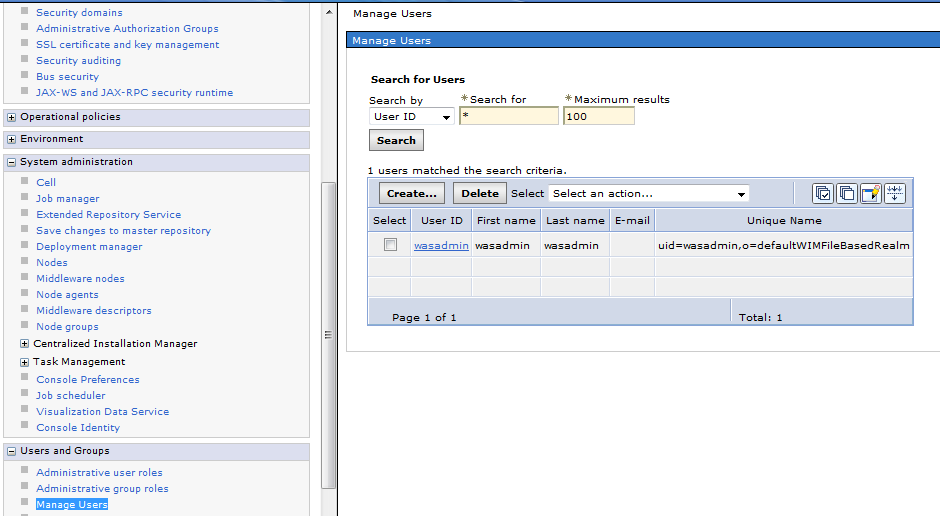
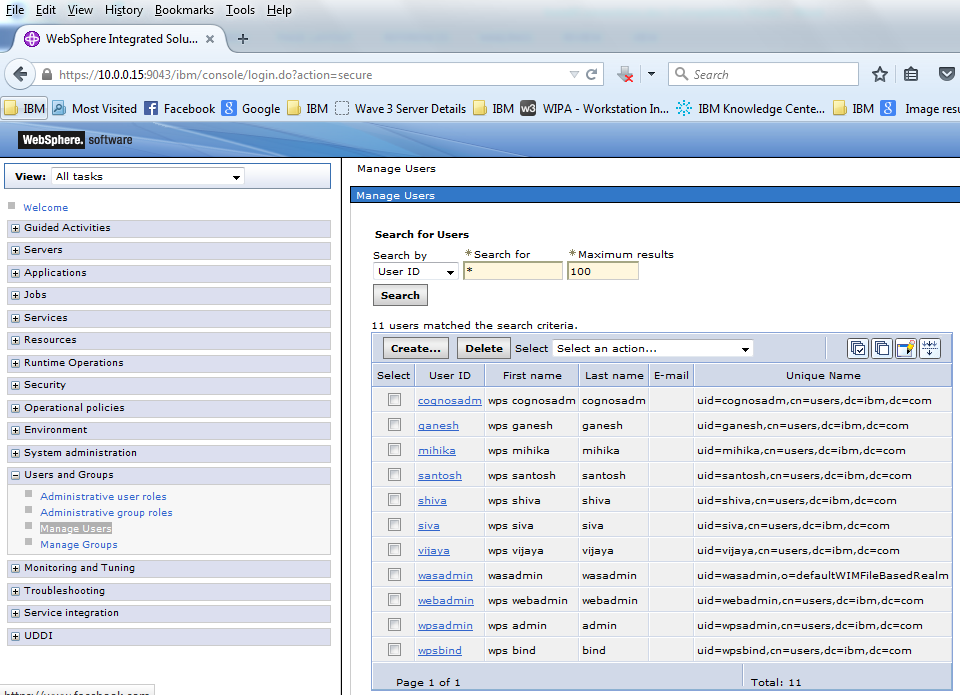
Just to check the list of users Navigate to Users and Group >> Manage Users
We see the List of users before the integration . Only “wasadmin” as File Based Realm
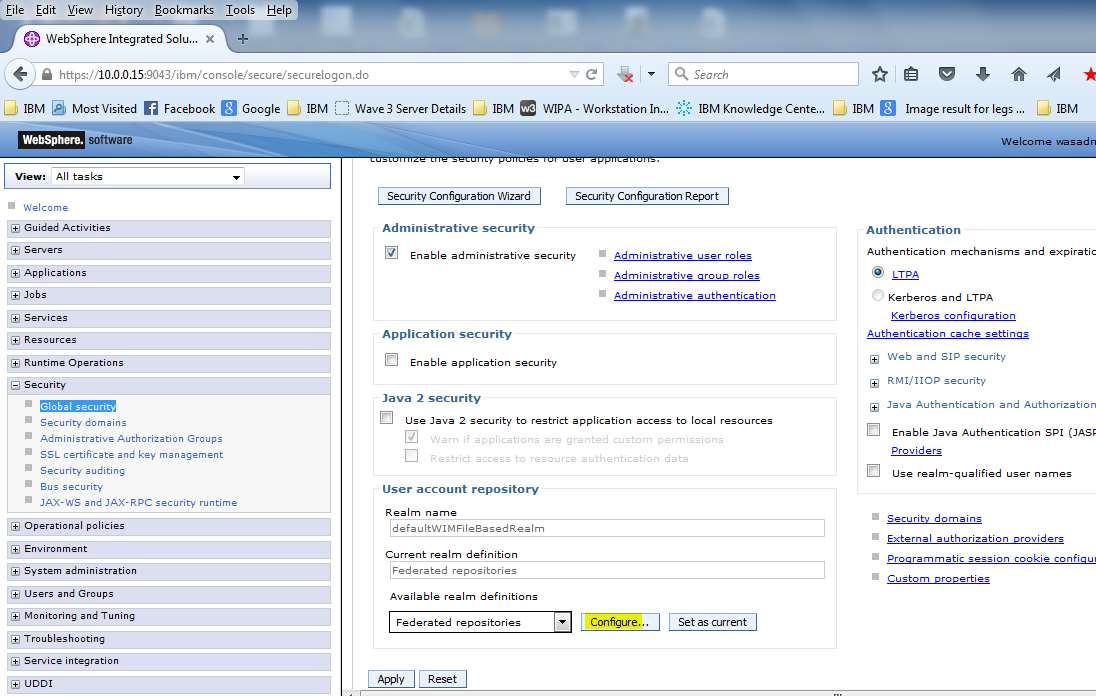
Step 5: To Integrate Ldap .. Click “Global Security “
Then Click “Configure” on the Federated Repositories
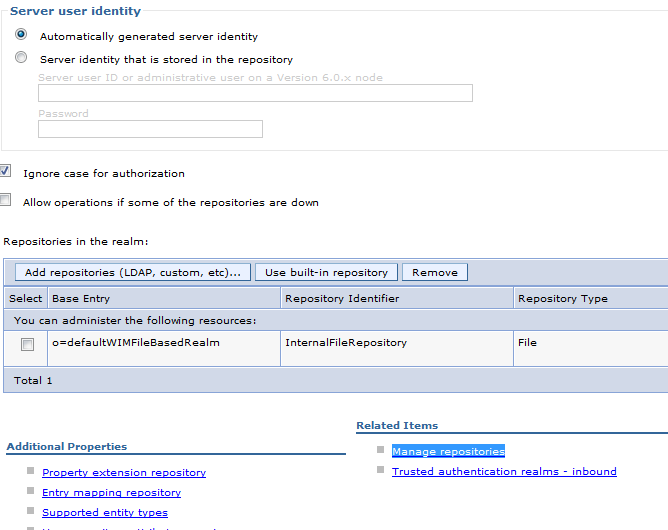
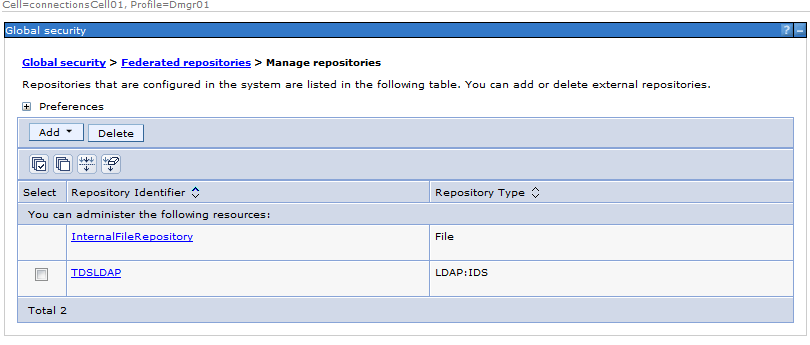
Step 6: Click on “Manage Repositories” as per the screenshot
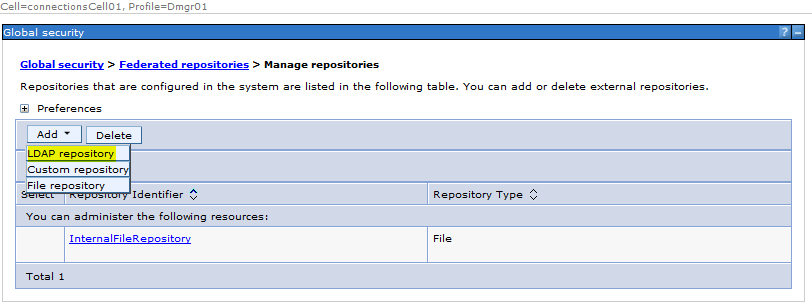
Step 7: Click “ADD” and , Select “LDAP repository” from the dropdown
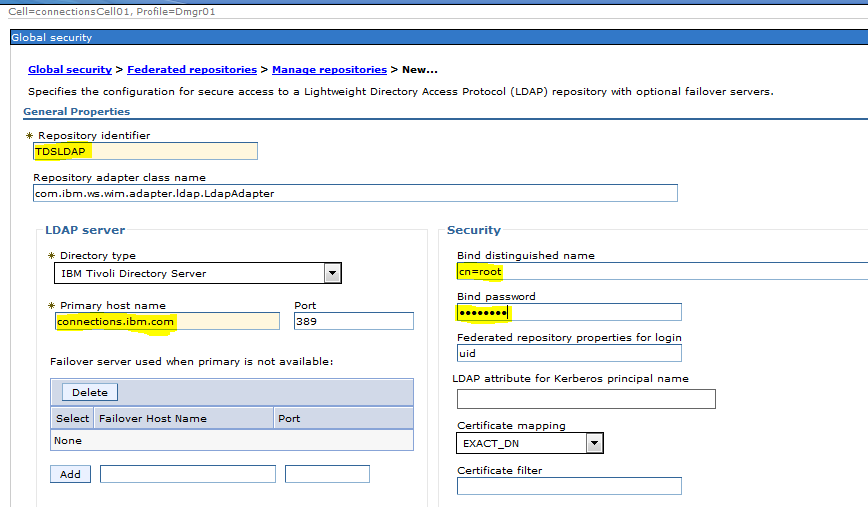
Step 8: This page we need to enter the details of the LDAP ( shared by Ldap team )
a ) Enter the LDAP Name ( Can be any name which will identify it . I have named it TDSLDAP )
b ) In the Drop Down Select “IBM Tivoli Directory Server “
c ) Enter the Bind Distintguised Name : cn=root
d ) Enter the Bind Password : password
e ) Here the Federated Repository properties for login is “uid” it might differ based on your environment it could be “cn” “email id ” etc
f ) Primary Host Name : connections.ibm.com ( you could provide the ip too )
g ) Port No : 389
i ) Click Apply and Save
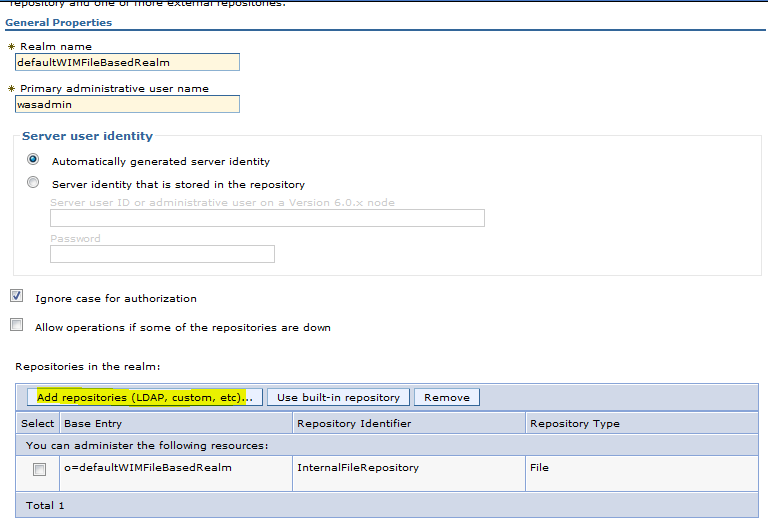
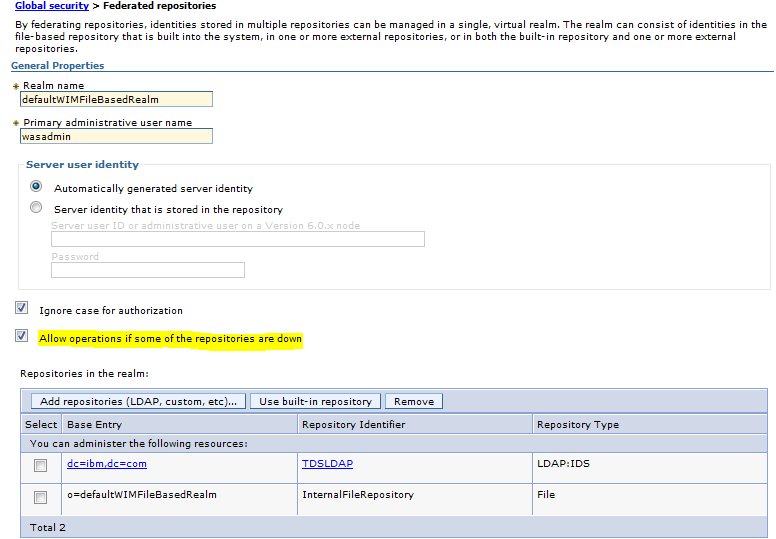
Step 9: Click on Global security > Federated repositories
Click on “Add Repositories ( LDAP custom etc )
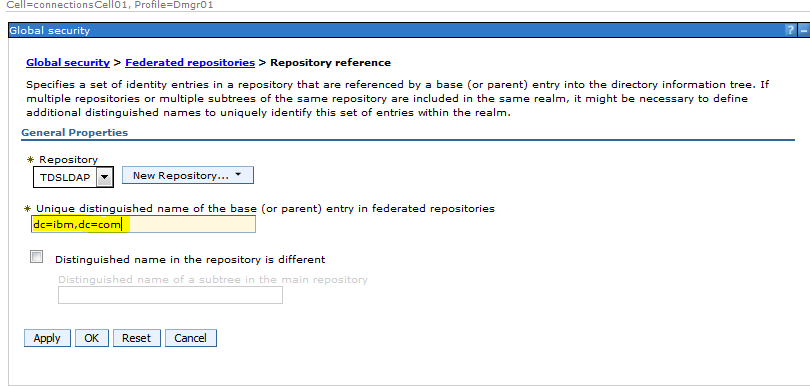
Step 10: From the drop Down Select “TDSLDAP”
Enter the Base DN in our case : dc=ibm,dc=com
Step 11: Click Apply and Save
Step 12: Check “Allow operations if some of the repositories are down”
This will enable us to login as wasadmin to the admin console even if the LDAP id down .
Step 13: Click Apply and Save
Step 14: Do full Synchronise
Step 15: Stop the Servers, Nodeagent and the Dmgr
Stop Servers
/opt/IBM/WebSphere/AppServer/profiles/Custom01/bin/stopServer.sh server1
Stop Nodeagent
/opt/IBM/WebSphere/AppServer/profiles/Custom01/bin/stopNode.sh server1
Stop Dmgr
/opt/IBM/WebSphere/AppServer/profiles/Dmgr01/bin/stopManager.sh
Step 16: Start the Dmgr , Nodeagent and Servers
Start Dmgr :
/opt/IBM/WebSphere/AppServer/profiles/Dmgr01/bin/startManager.sh
Start Nodeagent :
/opt/IBM/WebSphere/AppServer/profiles/Custom01/bin/startNode.sh
Start Server :
/opt/IBM/WebSphere/AppServer/profiles/Custom01/bin/startServer.sh server1
Check for any errors for LDAP etc in the SystemOut logs
Step 17: Validation : Now login with the file based registry user ie “wasadmin”
We can see the users from the LDAP and also wasadmin user from file based repository
Testing
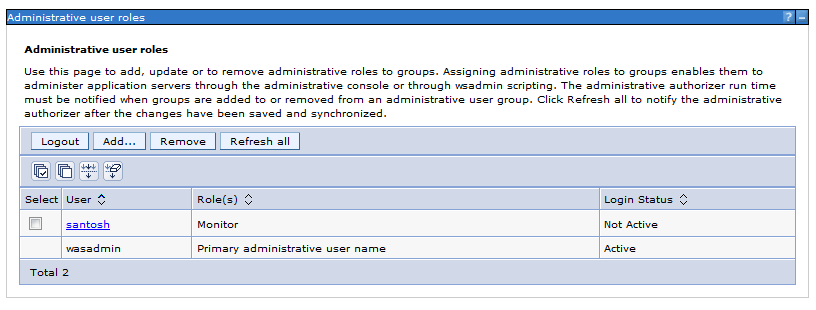
Test 1: We will add user “santosh” from the LDAP as a monitor role in WAS and test it
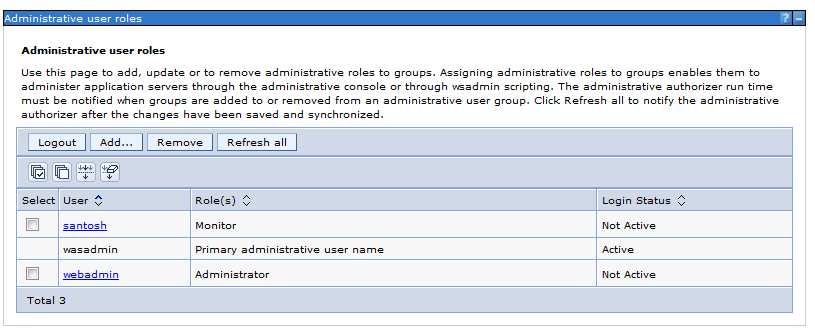
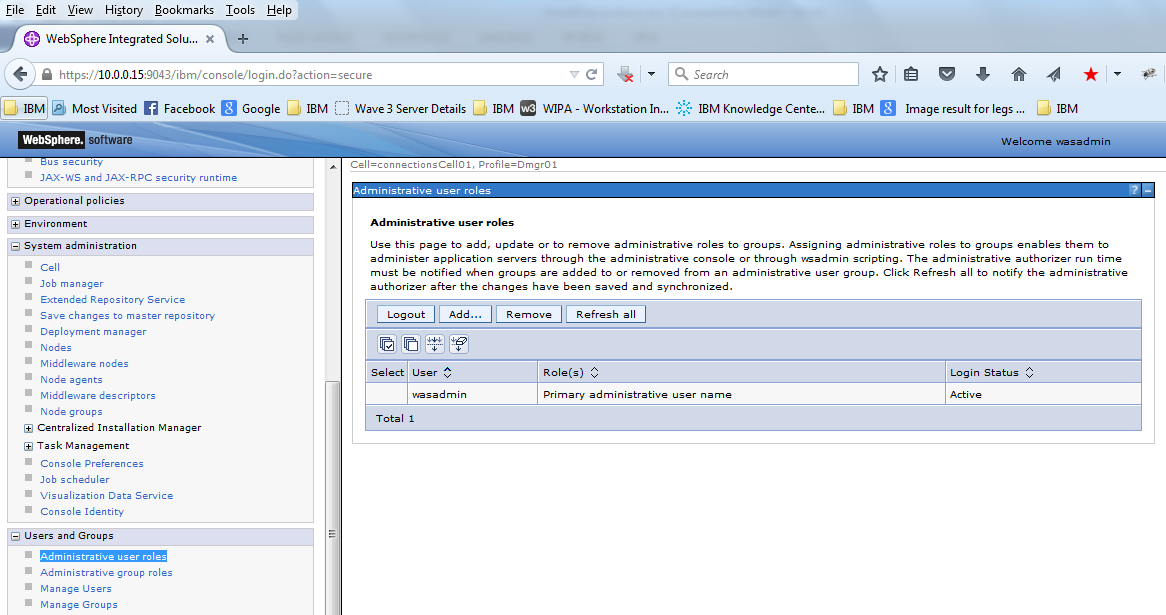
a ) Click User and Groups >> Administrative user Roles
Currently only “wasadmin” is available
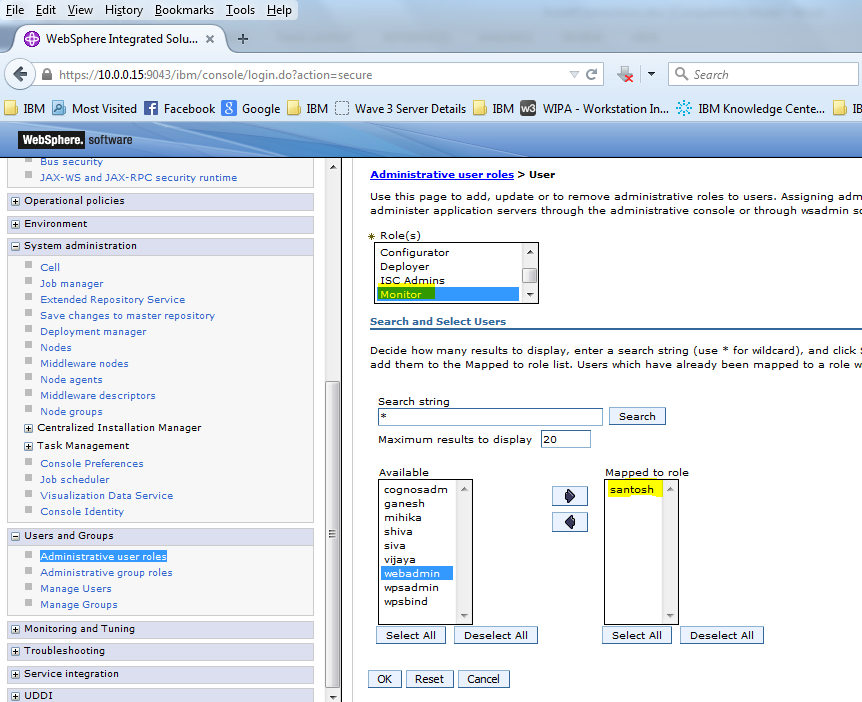
c ) Select “monitor” Role
Search the users using the Search button , We will be able to see the users from the ldap
Select “santosh” and drag it to the other side
Select OK and Save the configurations
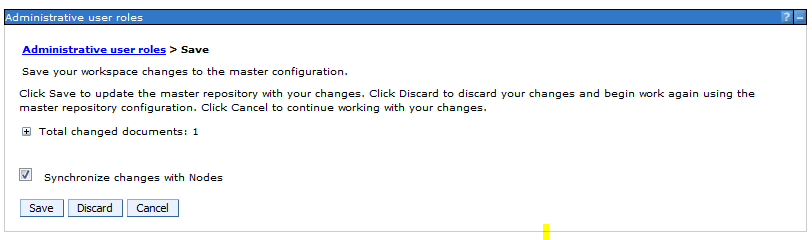
The user “santosh “ is added to the Administrative role as a “monitor” Role
d ) Now Logout
e ) Try login with user Santosh and password: password (As mentioned in the LDAP )
f ) We are able to login properly if all the setting are done correctly
g ) Navigate to other options and you will not see lots of options which were visible in the wasadmin login
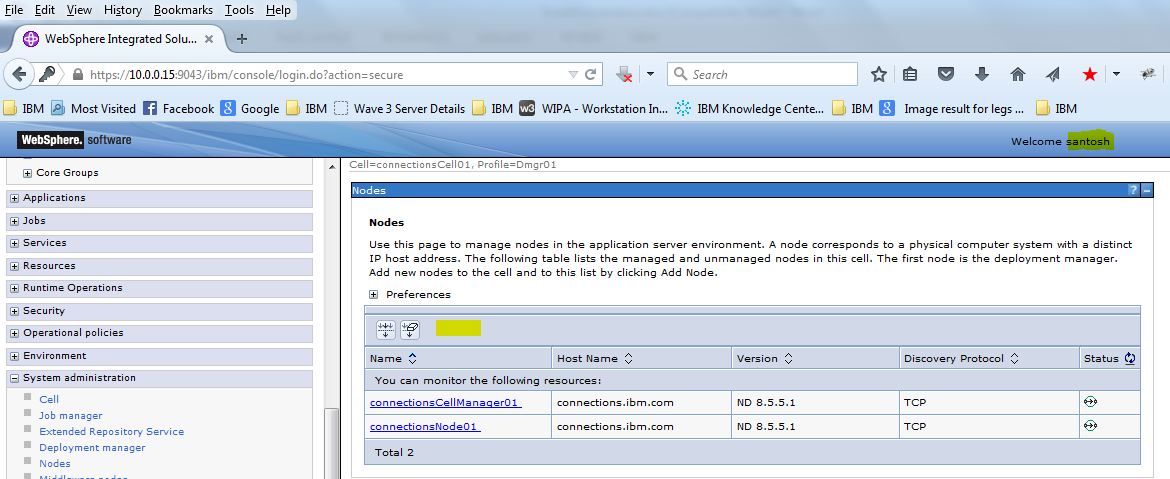
for eg under Nodes we dont see the options like Full Syncronise , Add etc
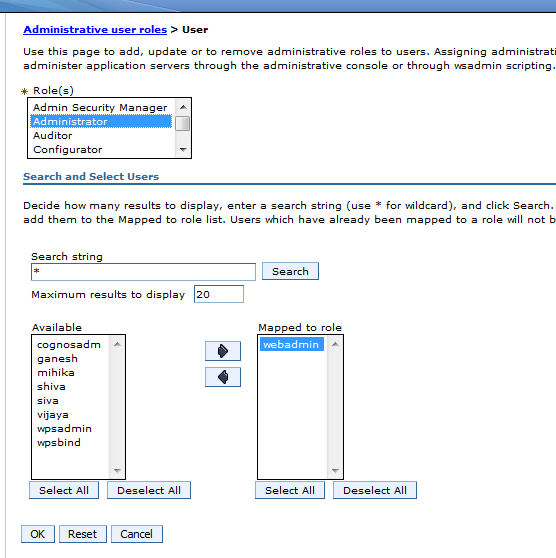
Test 2 : We will add webadmin this user is from the LDPA we will add it to the admin group
a) Click User and Groups >> Administrative user Roles
Currently only “wasadmin” is there
b ) Click Add ,
c ) Select “administrator” Role
Search the users using the Search button , We will be able to see the users there
Select “webadmin” and drag it to the other side
d ) Now Logout
e ) Try login with user webadmin and password: password (Password from the Ldap)
f ) We will see all the options which were available for wasadmin is also available for “webadmin“.
This is how we integrate TDS LDAP with Websphere Application Server . Similarly we can integrate any LDAP like Active Directory etc in a federated Repository .
To get regular mail updates on my Posts..
Please subscribe to the site http://webspherepundit.com
And also like the Facebook Page
https://www.facebook.com/webspherepundit